What Is the Most Effective Way of Securing Wireless Traffic
Enable WPA2 security for encryption. If youre really looking to secure network traffic consider using encryption.

Wi Fi Security Securing Your Wireless Network Businesstechweekly Com
Port 25 has been defined as the trigger port and port 113 as an open port.
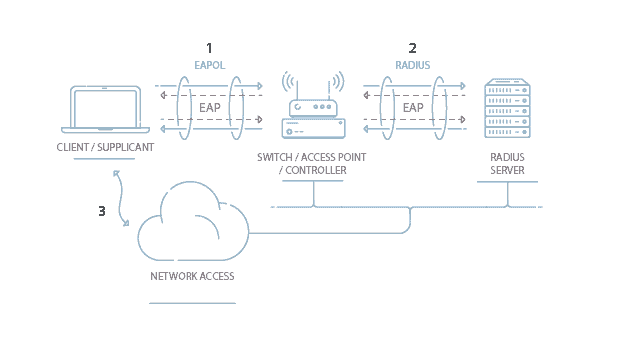
. Assess your cybersecurity. There are three main types of wireless security protocols and there are differences. Disabling the DHCP give static IP to your systems and enable ip address filtering is another way of doing it.
2 patterns in the programming code of the software on a computer. Which two conditions must be met for mobile device security measures such as remote lock and remote wipe to function. Implementing employee background checks.
Including security team members in the project management process. If a host infected with malware is causing a denial of service attack by flooding the network with traffic disconnecting the host from the network can stop the attack. Remember even with VLANs and 8021X authentication someone can.
Enable mac address filtering in router is one way of defending unauthorised attack. Instead Wi-Fi has become the go-to network access technology for users and endpoints. Install rogue antivirus software on the host.
Secure the wireless by putting complex password and change it atleast every3 or7 days. PKIs with OCSP supported. What is the most effective way of securing wireless traffic.
Wireless LANs or WLANs offer many advantages over. Deploying intrusion prevention systems. What is the most effective way of securing wireless traffic.
10TB for 398 for the first year is unmatched. The basic idea behind this technique is that like a wired network card all wireless NICs have a unique Media Access Control MAC address. What is the most effective way of securing wireless traffic.
A Wireless Intrusion Prevention System WIPS is a concept for the most robust way to counteract wireless security risks. Mary believes that her network was the target of a wireless networking attack. WPA2 is more secure than WEP or WPA for encrypting traffic.
Keep in mind many wireless routers and access points offer a WPAWPA2 and AESTKIP option. For many businesses wired Ethernet is no longer supreme. Carefully maintaining network firewall rules.
Open Network no security at all The best way to go is to deactivate Wi-Fi Protected Setup WPS and set the router to WPA2 AES. Perfect match for the super-easy SCEPman cloud PKI. WPA2 is more secure than WEP or WPA for encrypting traffic.
WPA2 is more secure than WEP or WPA for encrypting traffic. A WIPS is typically implemented as an overlay to an existing Wireless LAN infrastructure although it may be deployed standalone to enforce no. Please login or Register to submit your answer.
One of the more effective security techniques for securing wireless networks at the access point level is to use MAC address filtering. As you go down the list you are getting less security for your network. SSID and wireless MAC filtering are not encryption methods.
Some suggest using a layered approach to Wi-Fi security. Disable ActiveX and Silverlight on the host. Purpose Both WPA and WPA2 are supposed to secure wireless Internet networks from unauthorized access.
WPA2 is more secure than WEP or WPA for encrypting traffic. Ad 100 cloud based Radius SaaS for certificate based authentication for WIFI LAN and VPN. However there are protocols you can take that can improve security and protect your data from hackers and thieves.
IT Essentials v70 702. 1 a service pack. Log on to the host as a different user.
IDrive the cloud storage veteran delivers tons of storage online for an incredibly small outlay. 4 patches that prevent a newly discovered virus or worm from making a successful attack. Follow these wireless network security best practices to ensure your companys WLAN remains protected against the top threats and vulnerabilities.
SSID and wireless MAC filtering are not encryption methods. SSID and wireless MAC filtering are not encryption methods. I dont really disagree but I certainly suggest first ensuring you have enabled WPA2 security with AES encryption on any wireless network or SSID for private use.
Which two Windows default groups are allowed to back up and restore all files folders and subfolders regardless of what permissions are assigned to those files and folders. What is the most effective way of securing wireless traffic. Filter with MAC addres.
Which one of the following controls is the most effective way to protect against security-related architectural and design weaknesses. SSID and wireless MAC filtering are not encryption methods. All traffic that is sent out port 25 will open port 113 to allow inbound traffic into the internal.
WPA2 is more secure than WEP or WPA for encrypting traffic. Which one of the following security controls would be MOST effective in combatting buffer overflow attacks. What is the most effective way of securing wireless traffic.
Port triggering has been configured on a wireless router. SSID and wireless MAC filtering are not encryption methods. Based upon the Wireshark traffic capture shown here what type of attack likely took place.
Use VPNs to encrypt select PCs or servers. The main disadvantage of wireless networks is the lack of security. However such WIPS does not exist as a ready designed solution to implement as a software package.
Security Protocols for Wireless Networks. If you leave your router with no security then anyone can steal the.

Most Common Wireless Network Attacks Webtitan Dns Filter

Everything You Need To Know About Wireless Security


Comments
Post a Comment